August 28, 2020
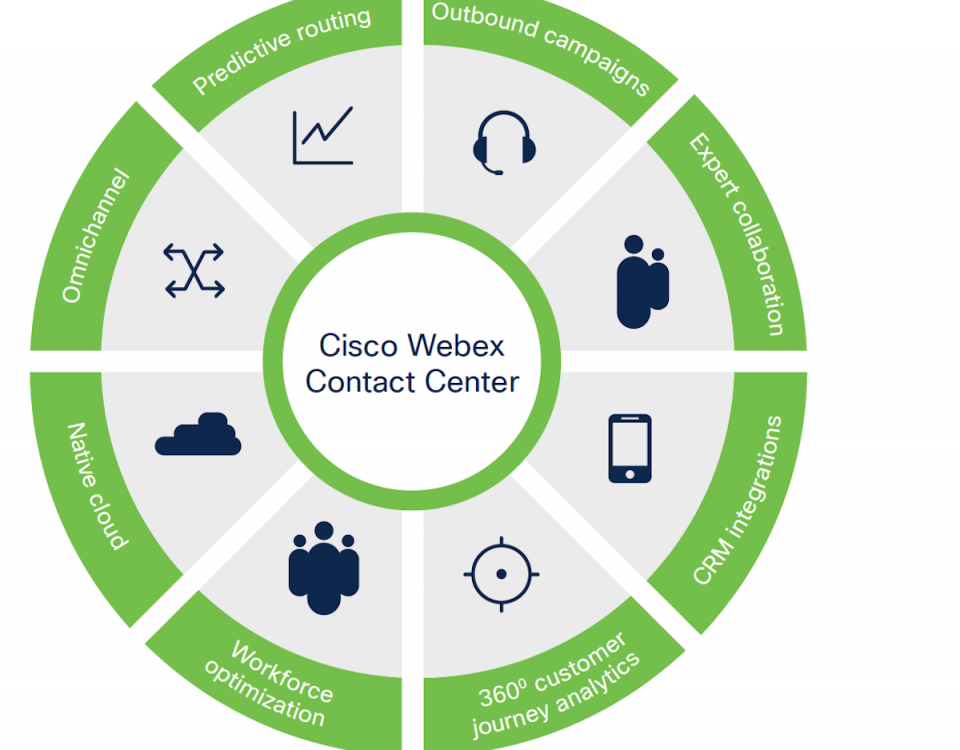
Optimize the performance of your contact center! Read this solution brief, brought to you by Pullin Cloud Technologies, to learn how @CiscoSMB Webex can improve the performance of your contact center—plus make it more agile and CX-focused. It does this thanks to an innovative set of capabilities, including outbound campaigns, native cloud, omnichannel, predictive analytics-based routing, agent and expert collaboration, business application integrations, 360-degree customer journey analytics, and a comprehensive WFH suite in a unified environment.